
Nowadays, the day to day life of most people is depended and governed by computer-based algorithms and information. This leads to the vital necessity of computer networking along with the role of network engineer at almost any organization. Intelligence Agencies also have to hire network engineers to maintain their highly secured networks. Working at that kind of organization may let the engineers work as a part of Mass Surveillance projects. This paper has critically analysed the ethical situation of being a network engineer at an intelligence agency from a neutral point of view.
Introduction
In the ancient world, the majority of humankind believed in a mysterious power called as magic which balances the good and bad in nature. According to Kizza (2014), ethics are also a relative, undefined human conduct that distinguishes and balance the good and bad in the corporate world along with the national laws and organizational policies. Individuals must follow their national law which is created and enforced by the government policymakers. Internal policies are defined by the organization and through the agreements like non-disclosure agreements, employees are legally bound to adhere to those policies. On the other hand, Ethics are not must to follow. Therefore, being an ethical or unethical professional is totally depending moral believes, religious beliefs and personal preference.
Kizza (2014) further explains that ethics were tried to be defined in many philosophical theories from Greek Athenian era, such as consequentialist theories which judge human actions based on the attainable consequences, deontological theories which categorize actions in to good and bad by considering the performer’s intentions to do so. Interception of computer networking and intelligence agencies make ethics a tremendous necessity for the wellbeing of the surrounded parties.
Intelligence agencies are the organizations that perform intelligence gathering on behalf of a state. Martin (2016) defines intelligence gathering as acquiring information and knowing about activities in a secret manner to improve national or international security. These intelligence agencies can be sorted in three levels according to its interests as below,
| Security Focus | British Agencies | American Agencies |
| Foreign | MI6 / SIS | CIA |
| Domestic | MI5 | FBI |
| Technical | GCHQ | NSA |
Network Engineers at Intelligence Agencies
These intelligence agencies use technology as their main path to achieve their goals. Therefore, the service of network engineers is heavily in demand in these institutes. Morris, Fustos and Haga (2012) mention that maintaining a reliable internal and internet-wide network connection by configuring network devices, and filtering and monitoring the traffic flow of the organization in order to achieve information assurance (Confidentiality, Integrity, and Availability) is the major responsibility of a network engineer. Being and a network engineer at an intelligence agency increases the severity of above-mentioned responsibility along with the ethical dilemma of the role without any argument.
The author would like to raise three most argumentative ethical issues that network engineers at intelligence agencies may encounter as below.
- Is monitoring and recording the network traffic ethical?
- Is exposing classified information in the agency’s servers to the public ethical?
- Is getting stored the civilians’ private data (Mass Surveillance) ethical?
Regardless of the industry, any network engineer has to face network monitoring and data breach-related issues. However, mass surveillance is a process that only the network engineers at intelligence agencies may experience. Therefore, a detailed discussion about mass surveillance and ethics is a successful attempt to fulfil the scope of this essay.
Mass Surveillance and Network Engineers
In modern technological arena, information is the most precious asset to be obtained. Gathering private information of civilians and local enterprises is one of the bittersweet actions that most intelligence agencies around the world are doing. In the industry, this process is called Mass Government Surveillance. Most of this information obtained to government servers from open databases and other digital sources. Therefore, network engineers have to widely involve in this data gathering/mining procedure.
According to Bowcott and Norton-Taylor (2016) intelligence agencies in the UK, especially Government Communications Headquarters (GCHQ) gathers personal data including passport information, travel records, emails, telephone conversations and financial data of British civilians since the 1990s. The following graphical representation unveils how the citizens in the UK aware and react to mass government surveillance.
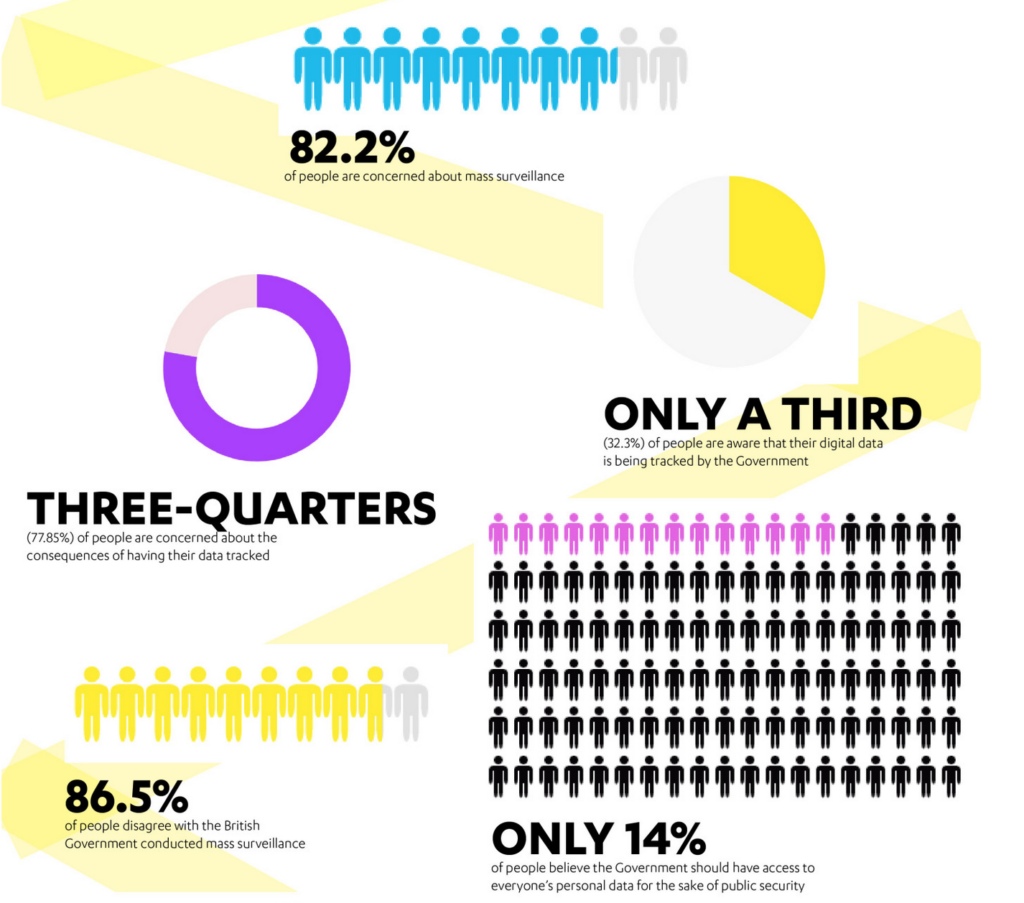
Even though mass surveillance sounds very negative process to civilians, there are advantages of it to civilians. The following table compares the advantages and disadvantages of mass government surveillance.
| Advantages | Disadvantages |
| Solving crimes and investigating incidents make efficient and accurate. | The government can become an authoritarian body which will have a limitless power to control citizens as its preference. |
| Tracing communications of suspected criminals and terrorists allows avoiding crimes at its planning phase. | Losing citizens’ privacy may cause negative psychological impacts on individuals. |
| Due to the probability of being caught under these circumstances, criminals are afraid to perform any crimes. | The collected information can be misused or compromised to an unauthorized party. |
| The acquired information can be contributed to academic research projects. | Maintaining a gigantic data storage like this is a very expensive project. |
(Netivist.org, 2018)
The laws to be concerned as a role in Mass Surveillance
Even though, individuals could be able to ignore ethics, the room to be ignored the laws of the country is very less. The author would like to dive into the legal framework of the UK because of its rich consistency of laws regarding computer networks. As mentioned by Jisc (2015), most fundament laws that are applied to computer networking are,
- Communication Act 2003 – Regarding the misusage of public communication.
- Data Protection Act 2018 – Regulations for storing personal data in a computer or a capable system.
- Privacy and Electronic Communications Regulation 2003 – describes restrictions to use personal data of individuals in electronic communications.
While these laws define penalties for general network usage, as explained by Wheelhouse (2015) the closest laws for mass surveillance is Regulation of Investigatory Powers Act (RIPA) 2000. The section 8(4) of this act enables public institutions to do mass surveillance under the approval of a Minister. Furthermore, he also has noted that the above-mentioned mass surveillance program (which is named as “Tempora”) of GCHQ was being alleged by many organizations for breaking Human Rights that is enforced by European Court.
Not only powerful countries like the United Kingdom, USA and Russia embraces these surveillance concepts to achieve the greater good to their nations, but also underdeveloped countries like Sri Lanka planning to powers up mass surveillance. A public revelation of Wikileaks.org. (2015) states a plan of Sri Lanka’s Ministry of Defence for locating an electronic surveillance & tracking system. As a result of this, new laws related to digital rights and surveillance will have to be introduced to the law of Sri Lanka.
Nevertheless, existing laws of any country would not be enough to save a network engineer to be tempted into misuse of mass surveillance. Therefore, intelligence agencies must impose their own internal policies to make their service more reliable to its citizens.
Ethical Dilemma of Mass Surveillance
Mass surveillance projects allow governmental bodies to have significant authoritarian power over its citizens. With this great power comes great responsibility for each individual who takes part in these projects including the network engineers. The great responsibility mentioned above demands ethical behaviour in a crucial manner. The best way to point out the ethical situation is The Snowden’s effect which is a real-life incident that took global attention to mass government surveillance procedure and methods of the United States.
Edward Snowden is one of the most popular whistle-blowers in the entire world history. As described by Carlson (2018) Snowden who is a former system administrator at CIA has exposed a significant amount of classified information related to surveillance projects of NSA. According to (Patsakis et al., 2018), this revelation negatively affected the foreign market of cloud services located in the USA. On the other hand, a great opportunity for the enterprises and start-ups opened to provide services and tools to ensure the cyber privacy of individuals all over the world. Meanwhile, the European countries pioneered to redo their laws of digital privacy by taking the Snowden’s effect as a precautional lesson.
Carlson (2018) further mentions that Snowden has carried out this by violating the country’s law, the Espionage Act of 1917. Majority of Americans considers as a traitor who tried to be a hero and some non-American people praise Snowden as a hero. Snowden was having a career in System Administration which is slightly related to computer networking. But with the network level authority, a network engineer could be able to cause bigger and better damage to the organization or impact to the worldwide community.
Being a part of these mass government surveillance in an intelligence agency puts a network engineer’s role at a stake in the ethical perspective. As explained above there are so many facts to concern this question is ethical or not. When diving into the core of this question, there is a greater good of this process that enhances the national security to the next level.
Conclusion
The ethics are being discussed by different philosophers from the ancient Greek era. Nowadays ethics are very important for professionals to make the right choice in their operations. Because of ethics employees do protests, get bullied, get rewards, be satisfied or leave their jobs. Network engineers play a big role at intelligence agencies to protect their nation’s security. At that service, they may have to interfere with mass government surveillance.
In an era where cyber crimes are rapidly growing, the intelligence agencies have to take huge responsibility on their shoulders and work to make sure their country is safe. At that point, expecting the network engineers at intelligence agencies or defence sector to be pure ethical figures is not a good identifier according to the author’s perspective of this matter. But being a Snowden or Jonny English who prioritize the security of the nation is sometimes a tough decision that every network engineer at intelligence agencies must take.
References
BOWCOTT, O. and NORTON-TAYLOR, R. (2016). UK spy agencies have collected bulk personal data since 1990s, files show. [online] the Guardian. Available at: https://www.theguardian.com/world/2016/apr/21/uk-spy-agencies-collected-bulk-personal-data-since-1990s [Accessed 31 Dec. 2018].
CARLSON, A. (2018). Edward Snowden: Traitor or Hero? – Ethics Unwrapped. [online] University of Texas at Austin. Available at: https://ethicsunwrapped.utexas.edu/case-study/edward-snowden-traitor-hero [Accessed 31 Dec. 2018].
GILBERT, D. (2014). Britain ‘Sleepwalked’ into Becoming a Mass Surveillance State. [online] International Business Times UK. Available at: https://www.ibtimes.co.uk/britain-sleepwalked-into-becoming-mass-surveillance-state-1470490 [Accessed 31 Dec. 2018].
JISC. (2015). Laws relevant to networking and computing. [online] Available at: https://www.jisc.ac.uk/guides/networking-computers-and-the-law/laws [Accessed 10 Jan. 2019].
KIZZA, J. (2014). Computer network security and cyber ethics. 4th ed. [ebook] Jefferson, North Carolina: McFarland, pp.17-24. Available at: http://libcat.staffs.ac.uk/cgi-bin/koha/opac-detail.pl?biblionumber=191375 [Accessed 20 Dec. 2018].
MARTIN, S. (2016). Spying in a Transparent World: Ethics and Intelligence in the 21st Century. Geneva Papers, [online] 19. Available at: https://www.gcsp.ch/News-Knowledge/Publications/Spying-in-a-Transparent-World-Ethics-and-Intelligence-in-the-21st-Century [Accessed 26 Dec. 2018].
MORRIS, G., FUSTOS, J. and HAGA, W. (2012). Preparing for a Career as a Network Engineer. Information Systems Education Journal, [online] 10, pp.13-20. Available at: http://isedj.org/2012-10/N1/ISEDJv10n1p13.html [Accessed 28 Dec. 2018].
NETIVIST.ORG. (2018). Mass government surveillance pros and cons: NSA spying. [online] Available at: https://netivist.org/debate/government-surveillance-pros-and-cons-nsa-spying [Accessed 31 Dec. 2018].
PATSAKIS, C., CHAREMIS, A., PAPAGEORGIOU, A., MERMIGAS, D. AND PIROUNIAS, S. (2018). The market’s response toward privacy and mass surveillance: The Snowden aftermath. Computers & Security, [online] 73, pp.194-206. Available at: http://www.sciencedirect.com/science/article/pii/S016740481730233X [Accessed 12 Jan. 2019].
WHEELHOUSE, A. (2015). The Legality of Mass Surveillance Operations. [online] Oxford Human Rights Hub. Available at: http://ohrh.law.ox.ac.uk/the-legality-of-mass-surveillance-operations/ [Accessed 10 Jan. 2019].
WIKILEAKS.ORG. (2015). WikiLeaks – The Hackingteam Archives. [online] Available at: https://wikileaks.org/hackingteam/emails/emailid/238000 [Accessed 10 Jan. 2019].




